Challenges With Private Key Protection
Arguably, the most critical aspect of any PKI system is the security placed on its private keys. The consequences of failing to protect the keys range from bad to downright catastrophic. While one could simply lock the private keys away in a secure offline box, this would make it difficult to use those keys in any meaningful way.
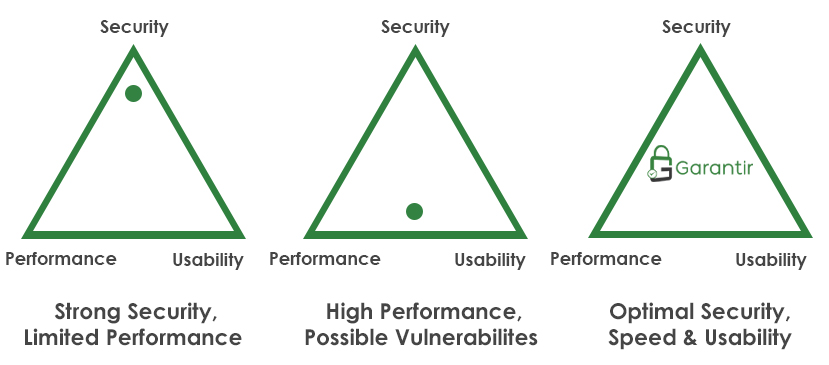
Indeed, this is a problem facing most organizations today. How can you balance the security and efficient use of the enterprise private keys? How do you make the private keys available to all of the clients that need signing access, while ensuring that the keys are never exposed? The primary challenge of InfoSec leaders across various industries is to achieve an optimal balance of security, performance, and usability.

Private Key Protection: Software vs. HSM
Software-Based Private Key Protection
Hardware Security Modules (HSM)
Solution: A Remote Digital Signature Platform